We hope you enjoyed CCM 4.0 mapping, Part Two: A technical dive into unified compliance strategy on May 13, 2021, 7:00 PM PDT at:
https://attendee.gotowebinar.com/register/4980569285837634829
After registering, the pre-meeting, presentation, and post-meeting are all on playback. We apologize for the glitch in editing. The session starts at minute 30. You are welcome to enjoy the presentation but please forward to minute 30 and feel free to stop viewing at minute 2:35:00.
We had an extra session with Eric Heitzman Director of Business Development. Eric helps Security Compass’s largest customers (in finance, technology, health, oil & gas) address Security, Privacy, and Compliance for software applications at scale. Eric is a career application security expert (security consulting, static analysis, and dynamic analysis).
Members of the ISC2 East Bay and ISACA Silicon Valley Community on April 29th had an opportunity to review reasons to quickly adopt the newly released Cloud Security Alliance, Cloud Controls Matrix V4.0 Cloud Controls Matrix (CCM), a Cybersecurity Control Framework (cloudsecurityalliance.org). As part one of a two-part discussion, that evening covered some of the common pitfalls that plague our efforts as a community, and as promised, this May 13th, 2-hour event offers a chance to continue with a deeper technical dive.
Outline
What Major Regulations Completely Changed over the last 24 months? Why update everything now? (What’s the domino effect of waiting?) Which are the key new requirements, such as Cryptographic Controls and new legal considerations for IoT? How are DevOps and SecOps better represented in the new standards? (NIST/CCM) Who and where are the working groups we can interact with to accomplish new mapping? What are the common pitfalls in the notation for ISO and NIST Standards? How can these be overcome?
Here’s are the Part One Slides: CSA CCM 4 Robin Basham ISACA SV April 28 2021
This Discussion covers that:
Major Cloud Providers expect to use ©Cloud Security Alliance, CCM 4.0 as the backbone supporting their Security Programs Policies, Programs, Audits
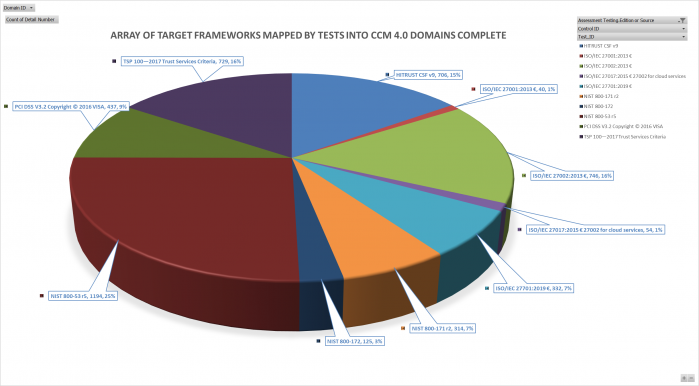
Leveraging existing AICPA SOC 2, HITRUST, PCI DSS V3.2.1, FedRamp, DFARS CMMC, ISO/IEC 27001 plus Privacy, Processing and Cloud requires a detailed understanding of these frameworks – i.e., experience completing engagements to do this work.*
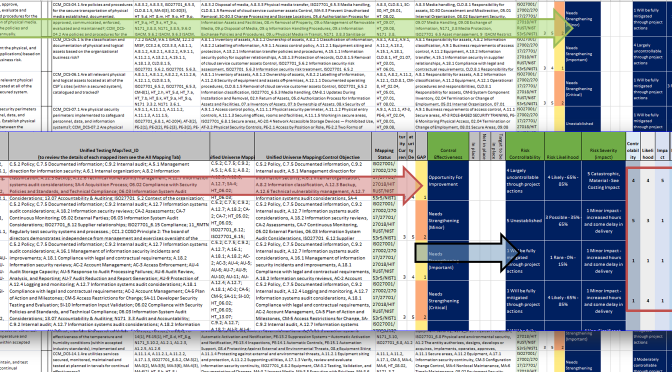
Creating useable cyber framework mapping is an exercise that drives common language across all Policies and Programs and is necessary to meaningful resilience and compliance. Volunteers generally can’t do it. Is increasingly necessary (CMMC)
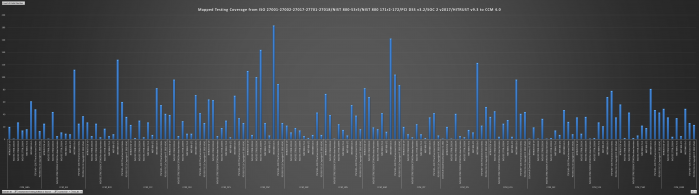
The available mappings offered by AICPA, NIST, HITRUST, and CSA have proven un-useful. As a community, it’s up to us to restore consumer confidence in using CCM 4.0 as a mapped framework. We also seek to support NIST expanded efforts for SP-800-53 r5, SP-800-53B, NIST SP-800-171r2, SP-800-172 Cybersecurity
So, what’s in the new standard and why is mapping so hard?
How can we effectively map this -> to that?
HITRUST CSF v9.3.1 © 2019 HITRUST
ISO/IEC 27001:2013 € Information security management systems — PIMS Requirements
ISO/IEC 27002:2013 € Information security management systems — Requirements
ISO/IEC 27017:2015 € 27002 for cloud services
ISO/IEC 27701:2019 € privacy information management — Requirements and guidelines
ISO/IEC 27018:2019 € (PII) in public clouds acting as PII processors
NIST 800-171 r2 Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
NIST 800-172 Enhanced Security Requirements for Protecting Controlled Unclassified Information
NIST 800-53 r5 Security and Privacy Controls for Information Systems and Organizations
PCI DSS V3.2.1 Copyright © 2018 VISA
2017 Trust Services Criteria © 2017 AICPA
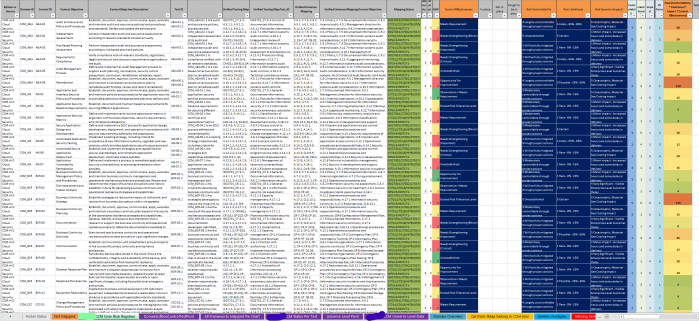
| Audit and Assurance – A&A | Audit and Assurance Policy and Procedures; Independent Assessments; Risk-Based Planning Assessment; Requirements Compliance; Audit Management Process; Remediation |
| Application and Interface Security – AIS | Application and Interface Security Policy and Procedures; Application Security Baseline Requirements; Application Security Metrics; Secure Application Design and Development; Automated Application Security Testing; Automated Secure Application Deployment; Application Vulnerability Remediation |
| Business Continuity Management and Operational Resilience – BCR | Business Continuity Management Policy and Procedures; Risk Assessment and Impact Analysis; Business Continuity Strategy; Business Continuity Planning; Documentation; Business Continuity Exercises; Communication; Backup; Disaster Response Plan; Response Plan Exercise; Equipment Redundancy |
| Change Control and Configuration Management – CCC | Change Management Policy and Procedures; Quality Testing; Change Management Technology; Unauthorized Change Protection; Change Agreements; Change Management Baseline; Detection of Baseline Deviation; Exception Management; Change Restoration |
| Cryptography, Encryption and Key Management – CEK | Encryption and Key Management Policy and Procedures; CEK Roles and Responsibilities; Data Encryption; Encryption Algorithm; Encryption Change Management; Encryption Change Cost Benefit Analysis; Encryption Risk Management; CSC Key Management Capability; Encryption and Key Management Audit; Key Generation; Key Purpose; Key Rotation; Key Revocation; Key Destruction; Key Activation; Key Suspension; Key Deactivation; Key Archival; Key Compromise; Key Recovery; Key Inventory Management |
| Datacenter Security – DCS | Off-Site Equipment Disposal Policy and Procedures; Off-Site Transfer Authorization Policy and Procedures; Secure Area Policy and Procedures; Secure Media Transportation Policy and Procedures; Assets Classification; Assets Cataloguing and Tracking; Controlled Access Points; Equipment Identification; Secure Area Authorization; Surveillance System; Unauthorized Access Response Training; Cabling Security; Environmental Systems; Secure Utilities; Equipment Location |
| Data Security and Privacy Lifecycle Management – DSP | Security and Privacy Policy and Procedures; Secure Disposal; Data Inventory; Data Classification; Data Flow Documentation; Data Ownership and Stewardship; Data Protection by Design and Default; Data Privacy by Design and Default; Data Protection Impact Assessment; Sensitive Data Transfer; Personal Data Access, Reversal, Rectification and Deletion; Limitation of Purpose in Personal Data Processing; Personal Data Sub-processing; Disclosure of Data Sub-processors; Limitation of Production Data Use; Data Retention and Deletion; Sensitive Data Protection; Disclosure Notification; Data Location |
| Governance, Risk and Compliance – GRC | Governance Program Policy and Procedures; Risk Management Program; Organizational Policy Reviews; Policy Exception Process; Information Security Program; Governance Responsibility Model; Information System Regulatory Mapping; Special Interest Groups |
| Human Resources – HRS | Background Screening Policy and Procedures; Acceptable Use of Technology Policy and Procedures; Clean Desk Policy and Procedures; Remote and Home Working Policy and Procedures; Asset returns; Employment Termination; Employment Agreement Process; Employment Agreement Content; Personnel Roles and Responsibilities; Non-Disclosure Agreements; Security Awareness Training; Personal and Sensitive Data Awareness and Training; Compliance User Responsibility |
| Identity and Access Management – IAM | Identity and Access Management Policy and Procedures; Strong Password Policy and Procedures; Identity Inventory; Separation of Duties; Least Privilege; User Access Provisioning; User Access Changes and Revocation; User Access Review; Segregation of Privileged Access Roles; Management of Privileged Access Roles; CSCs Approval for Agreed Privileged Access Roles; Safeguard Logs Integrity; Uniquely Identifiable Users; Strong Authentication; Passwords Management; Authorization Mechanisms |
| Interoperability and Portability – IPY | Interoperability and Portability Policy and Procedures; Application Interface Availability; Secure Interoperability and Portability Management; Data Portability Contractual Obligations |
| Infrastructure and Virtualization Security – IVS | Infrastructure and Virtualization Security Policy and Procedures; Capacity and Resource Planning; Network Security; OS Hardening and Base Controls; Production and Non-Production Environments; Segmentation and Segregation; Migration to Cloud Environments; Network Architecture Documentation; Network Defense |
| Logging and Monitoring – LOG | Logging and Monitoring Policy and Procedures; Audit Logs Protection; Security Monitoring and Alerting; Audit Logs Access and Accountability; Audit Logs Monitoring and Response; Clock Synchronization; Logging Scope; Log Records; Log Protection; Encryption Monitoring and Reporting; Transaction/Activity Logging; Access Control Logs; Failures and Anomalies Reporting |
| Security Incident Management, E-Discovery, and Cloud Forensics – SEF | Security Incident Management Policy and Procedures; Service Management Policy and Procedures; Incident Response Plans; Incident Response Testing; Incident Response Metrics; Event Triage Processes; Security Breach Notification; Points of Contact Maintenance |
| Supply Chain Management, Transparency, and Accountability – STA | SSRM Policy and Procedures; SSRM Supply Chain; SSRM Guidance; SSRM Control Ownership; SSRM Documentation Review; SSRM Control Implementation; Supply Chain Inventory; Supply Chain Risk Management; Primary Service and Contractual Agreement; Supply Chain Agreement Review; Internal Compliance Testing; Supply Chain Service Agreement Compliance; Supply Chain Governance Review; Supply Chain Data Security Assessment |
| Threat and Vulnerability Management – TVM | Threat and Vulnerability Management Policy and Procedures; Malware Protection Policy and Procedures; Vulnerability Remediation Schedule; Detection Updates; External Library Vulnerabilities; Penetration Testing; Vulnerability Identification; Vulnerability Prioritization; Vulnerability Management Reporting; Vulnerability Management Metrics |
| Universal Endpoint Management – UEM | Endpoint Devices Policy and Procedures; Application and Service Approval; Compatibility; Endpoint Inventory; Endpoint Management; Automatic Lock Screen; Operating Systems; Storage Encryption; Anti-Malware Detection and Prevention; Software Firewall; Data Loss Prevention; Remote Locate; Remote Wipe; Third-Party Endpoint Security Posture |
Your speaker tonight is ISC2 East Bay’s own, Robin Basham, Owner EnterpriseGRC Solutions, President, ISC2 East Bay, Certified Information Systems Security (CISSP), Audit (CISA), Governance (CGEIT) and Risk (CRISC), and GRC expert. Robin recently contributed a mapping refresh for NIST 171/172 to Dr. Ron Ross FISMA team and is currently contributing to the CCM Mapping for version 4.0. She is also a past board member of the ISACA SV Chapter.