Attention: We are at capacity. If you recieved an email stating you have a badge, you can come. If you have not been notified that you have a badge waiting, sorry, we are full.
Full attendance for registered ISC2 members earns 8 CPE. Certificates of attendance can be used with organizations that recognize ISC2 for professional development credits.
Venue: Oracle, Pleasanton – address, and map 5815 Owens Dr, Pleasanton, CA 94588
- 8 CPE Event – Pricing for (ISC)2—ISACA—ISSA Members – $55.00 USD
- Students – $35.00 USD
- Non-Members – $75.00 USD
- Recent Past Presenters FREE (to see if you qualify, look at the Chapter Events page)
- Member Sponsors (Paying it forward) $100.00 USD as a charitable donation.
Our single-day event sponsor rates are:
- Breakfast $300.00 (Thank you, Otorio)
- Lunch $500.00 (Thank you, ColorTokens)
- Coffee and Bronze Sponsor $500.00 (Thank you, Securonix, our lifetime Platinum sponsor.
For more information about sponsoring the ISC2 East Bay Chapter and or any of the Chapter events, email: conferencedirector@isc2-eastbay-chapter.org (also, Robin, (ISC)2 East Bay Chapter President).
*Time spent one-on-one with Sponsors may count as an offset towards up to 1.5 hours of the day’s 8 CPE.
Visit: OTORIO—COLORTOKENS – SECURONIX for up to 1.5 CPE as an alternative to time attending all of the presentations, during the breaks, or to be completed independently within one week of the event. (Requires email to the conference director.)
| Topics and Companies (Still under development, please check back soon.) | Speakers and links to bios |
|---|---|
| 8 AM Sponsor Address: Why we work with ISC2 East Bay and Who we are, from OTORIO. This is an open forum during sign-in and seating from 8 to 8:55 About Jackie Kalter: Jackie Kalter has been a strategic Sales Executive in Cybersecurity for over 20 years and is currently a Director of Sales for OTORIO. She has previously served on the Board of ISSA Orange County in the capacity of VP and Program Director, | Jackie Kalter and is currently President of the Cloud Security Alliance (CSA) in Orange County and serves on the Board for CSA San Diego. Additionally, she founded a Women’s Leadership Group in OC and San Diego. |
| OTORIO and our sibling organizations, CSA, ISACA, ISSA, and fellow chapters of ISC2 welcome you to breakfast and coffee 8:00 – 8:55 AM | Enjoy your coffee and a bagel, or yogurt and fruit, a morning meal from the people at OTORIO.  When sitting in the meeting room or gathering in close proximity, please wear a mask. Although most of us are vaccinated, some of our members are immunocompromised. |
| 9 AM Topic: Zero Trust in a Converging World OTORIO’s Domain expertise within Operational Technologies will be demonstrate Zero Trust ramifications in a Converging World. This presentation explains how IT and IoT can come together and deploy a Zero Trust architecture in a secure manner that allows for resilient operations. About Philippe Pagnier: Philippe Pagnier has been in the Operational Technology space for over 25 years, with more than half of that time focused on OT networks in | Philippe Pagnier utilities, manufacturing, and telecommunications. Philippe is currently applying his extensive knowledge as Senior Cybersecurity Engineer at OTORIO. Philippe attended the National School of Applied Science and Technology in France, earning his MSEE, Engineering with an emphasis on Industrial Computing and Digital Signal Processing. |
| About OTORIO: We empower operational and security teams to proactively manage digital risks and build resilient operations through a technology-enabled ecosystem. Our OT security and converged OT-IT-IIoT network risk management solutions are selected and deployed worldwide by industrial manufacturing, critical infrastructure, smart transportation organizations, and more. |  |
| 10 AM Topic: Implementing Zero Trust With traditional perimeter-based and endpoint security, enterprises protect the entry into and egress from the network, define and group devices/users into subnets/VLANs using a specific set of usually static rules, use authentication mechanisms centered around users, and install agents to detect and prevent malware. These methods, though necessary, are not enough to protect against the threats posed by unmanaged devices, IoT devices, credential misuse, wrong configuration, insider mal-intent, and lateral movement of threats once they enter the system. Thus, a zero-trust way of implementing security is gaining strong momentum. Zero Trust is rooted in the principle of “Always verify, never trust” and is designed to address security, access privileges, and control in the network by leveraging micro-segmentation and performing granular access enforcement based on users, devices, data, and location properties. In this talk, we will focus on implementing zero trust for IoT devices | Srinivas Akella About Srinivas Akella: Srinivas is an entrepreneur and a technologist with a strong cyber security, cloud, and SaaS background. He founded WootCloud Inc, an IoT Security company. In this role, he has architected the WootCloud product line and oversaw the execution of all phases of products and solutions across WootCloud’s IoT Security portfolio. WootCloud is now acquired by Netskope Inc. Srinivas has over 25 years of experience in Engineering and Leadership roles. He holds four patents in IoT Security. His most recent roles have been in the cyber security industry as CTO/CPO, CEO at WootCloud, Principal Engineer at Elastica ( BlueCoat, Symantec), Qualys, and Webroot. |
| About Wootcloud and its acquisition by Netskope: https://www.netskope.com/blog/netskope-acquires-wootcloud-an-innovator-in-enterprise-iot-security?  | WootCloud is proud to become a part of Netskope and extend #zerotrustsecurity to Devices and IoT – together we have the most comprehensive vision in the security industry – reach out to us for more details on how the new entity can help you with your cyber sec challenges!! |
| 11 AM Topic: Zero Trust as a Platform Zero Trust requires the ability to adhere to the government mandate set by NIST directive 800-207 which examines the 7 Pillars of zero trust. ColorTokens will address 5 Pillars of the Zero Trust model We have designed the Platform to be Simplified, Visible, and Easy to enforce your security policy. The intention is to be able to detect threats and examine and contain the threat. ColorTokens looks at Zero Trust from North to South and East to West traffic. Unless verified, we implicitly deny all users, devices, network, cloud, and API services. The only way to keep attackers from attacking is to ensure your network is invisible and when visible granularity limits the space they can travel. You may know this as micro-segmentation. ColorTokens can micro-segment users, devices, network layers, Cloud layers, and now API-based services in containers. | Erica Cunningham Erica Cunningham-Is currently the Northwestern Regional Sales Manager for ColorTokens (Zero-Trust) Platform. She has also been a Cyber Security Sales Director for the past 20 years helping Enterprise Companies meet their Security and Compliance goals. She has served on the ISSA SF Chapter board for 7 years. She is currently the VP of the ISC2 East Bay chapter. Erica holds a Bachelor of Science in Information Systems and a Master of Science in Cyber Security. |
| Co-presenting and performing the technical demo is our own member, Venky Raju, CISSP (LinkedIn title includes: while (True) { learn(); make(); hack(); teach(); lead() }). Venky is ColorToken’s Field CTO, and (ISC)2 Silicon Valley’s Membership Director. You may recall that Venky was the ISC2 East Bay Hackathon winner. Venky is a technologist passionate about cybersecurity and secure software development. As Field CTO of ColorTokens, he evangelizes the need for a proactive, Zero Trust-based approach to cybersecurity and showcases ColorTokens’ innovative platform in addressing modern threats. | Before ColorTokens, Venky was a founding member of Samsung Knox, the world’s first secure Android platform now deployed in billions of Samsung Galaxy devices. s from (ISC)². He also led global R&D teams at Samsung Electronics and Nortel Networks developing cutting-edge networking systems and services. He is a named inventor in several networking and consumer electronics patents. In addition, he holds the CISSP and CCSP certification Venky Raju  |
| About ColorTokens: ColorTokens simplifies, accelerates, and automates your security operations with our award-winning Xtended ZeroTrust PlatformTM. With us, your business is resilient to cyber threats, each critical asset completely secure, and assured against any misadventure from anywhere. | Our ColorTokens unique Zero Trust approach gives you the comfort and confidence of fully protected cloud workloads, dynamic applications, endpoints, and users. |
| Noon: The Future of Zero Trust, ColorTokens Lunch is Barb-B-Q from Armadillo Willy’s and Sponsor Address from Erica Cunningham. People who want a Vegan option can let us know at the start of the day and we’ll give them tokens (from ColorTokens) to get lunch from the Oracle Cafeteria. Lunch is an open hour so there’s plenty of time to socialize and enjoy your lunch options. When sitting in the meeting room or gathering in close proximity, please wear a mask. Although most of us are vaccinated, some of our members are immunocompromised. |    |
| 1 PM Topic: What is data for good and how will we trust it? -Web data as essential business insights -The various uses of web data and technical ways of its sourcing and structure -The role of data in the data pillar of Zero Trust About Ben Segal: Ben Segal is a focused, performance-driven leader with thorough knowledge of technical processes for enterprise software, SaaS applications, and digital platforms. With a proven track record of ramping quickly and developing urgency in sales cycles, Ben is known for his strong team-building experience with decisive judgment and discipline to focus on driving complex sales implementations. | Benjamen Segal Ben has comprehensive experience in both large, global organizations and emerging growth companies. He is the former VP of Sales with adtech pioneer IPONWEB, and held sales leadership roles with VC-backed enterprise SaaS platforms in the ad tech, martech, and HRIS spaces. Ben also worked for Salesforce during their years of rapid expansion. Ben has a graduate degree in Business from Columbia University. |
| About Bright Data: Bright Data is the pioneer and innovator in data collection automation, dedicated to helping all businesses view the Internet just like their consumers and potential consumers do each and every day. We help global brands gather publicly available online data in an ethical manner at scale. Working with over 10,000 customers, our data collection automation (DCA) platform enables clients to view the internet in complete transparency. By scouring the web through the eyes of the consumer, organizations can turn unstructured | HTML data at scale into structured CSV or JSON databases. This helps deliver business insights, from how your customers are interacting with your brand and what share of voice your competitors hold. Ultimately, this translates to making better, faster, and more informed business decisions based on data that is real-time, accurate, large-scale, and transparent. |
| 2 PM Topic: When the Cyber War Was Zero Trust Zero Trust is revolutionizing network security architecture: it is data and device-centric and designed to stop data breaches while protecting critical infrastructure and making cyber attacks unsuccessful. In this session, Zero Trust Creator, John Kindervag, SVP of Cybersecurity Strategy at ON2IT, will discuss the concept of Zero Trust and explain why Zero Trust is the world’s only true cybersecurity strategy. In 2020, President Biden issued an Executive Order mandating that all US Federal Government Agencies move towards adopting Zero Trust. Zero Trust is strategically resonant to the highest levels of the business and practically and tactically implementable using commercial off-the-shelf technologies. These 21st-century networks have been adopted by large enterprises and government entities around the world. John will explain how a Zero Trust Network Strategy will achieve tactical and operational goals that make security organizations business enablers, not business inhibitors. About John Kindervag: Senior Vice President Cybersecurity Strategy, ON2IT, and ON2IT Global Fellow John Kindervag joined ON2IT in March of 2021 as Senior Vice President Cybersecurity Strategy and ON2IT Global Fellow. | John Kindervag Previously John Kindervag was Field CTO at Palo Alto Networks and a Vice President and Principal Analyst at Forrester Research. John is considered one of the world’s foremost cybersecurity experts. He is best known for creating the revolutionary Zero Trust Model of Cybersecurity. In 2021, John was named to the President’s NSTAC Zero Trust Sub-Committee and was a primary author of the NSATC Zero Trust report being delivered to the President of the United States. Additionally, John was named CISO Magazine’s 2021 Cybersecurity Person of the Year. John has a practitioner background, serving as a security consultant, penetration tester, and security architect. He has been interviewed and published in numerous publications and has also appeared on television networks. He is a frequent speaker at security conferences and events. |
 We are also honored to meet KRISTIE BELL, the Chief Executive Officer of ON2IT Inc., leading the North American expansion of global pure-play managed cybersecurity services company, ON2IT BV Group. With more than 30 years in global corporate executive roles, Kristie has extensive worldwide experience in building long term strategic client partnerships and business technology alliances across all industries. She is deeply passionate about cybersecurity and committed to working with ON2IT customers to embrace Zero Trust to strengthen their security postures. In 2014, Kristie retired from IBM where she was the Vice President of Global Sales for IBM’s Systems & Technology Group, driving sales initiatives around the world for IBM’s $14B systems business. During her tenure at IBM, she held several global leadership | positions and was responsible for multibillion-dollar business portfolios. She led teams that delivered strong business results through creative solutions to difficult technology issues, while maintaining the highest levels of customer satisfaction. Kristie served as a Vice President in IBM’s Global Technology Services and Systems & Technology Groups, transforming channel sales execution models in both groups and leading IBM’s storage division in Europe, Middle East and Africa to market share growth. Kristie is also an award winning and published photographer, often utilizing her photographic talents to support her church and local youth musical theatre nonprofit organizations. She and her family of filmmakers currently reside in Southern California. |
| About ON2IT Cybersecurity: ON2IT is a global pure-play cybersecurity service provider. We offer worldwide managed cybersecurity services for organizations with complex and dynamic IT infrastructures. | ON2IT managed services are modular, scalable, cost-effective, and always based on Zero Trust. |
| 3 PM Diving into the pillars, meeting with the experts over Coffee and Cake | Use your appointment card to verify a conversation to cover every pillar of Zero Trust |
 When sitting in the meeting room or gathering in close proximity, please wear a mask. Although most of us are vaccinated, some of our members are immunocompromised. | ISC2 East Bay Breaks for Cake During our extended networking hour attendees will have access to upload notes from Vendor 1-on-1s which may account for up to 1.5 alternative credits. |
| The coffee break Sponsor is Securonix, who seeded this chapter with a Platinum Sponsorship and is our lifetime partner for all things SIEM. Thank you, Jamie! | Don Hewitt and Brian Albrecht  |
| About Securonix: Securonix Inc (Securonix) is a security intelligence solutions provider. It enables users to detect, track, evaluate, and challenge security threats and risks. The company’s product portfolio includes Securonix Next-Gen SIEM, Securonix UEBA, Securonix SOAR, Securonix NTA, and Securonix Security Data Lake. Securonix offers solutions such as application security, Securonix for AWS, cloud security monitoring, Securonix for CrowdStrike, cyber threat, data exfiltration, Securonix for | EMR applications, fraud prevention, insider threats, Securonix for healthcare, identity analytics, and intelligence, insider threat, Securonix for Office 365, Securonix for Okta, privileged accounts, and Securonix for PTC windchill. Securonix is headquartered in Addison, Texas, the US. |
| Earn .5 CPE for every half hour spent with an ISC2 East Bay Sponsor | Thank you to Oracle for the generous use of your facilities! |
| 4 PM Topic: Big Breaches This talk covers the key lessons learned and root causes of the biggest mega-breaches and the 9,000+ reported breaches over the past 15 years. By analyzing the histories, stories, and deep dives of breaches such as those at Target, JPMorgan Chase, OPM, Yahoo, Equifax, Facebook, Marriott, and Capital One, as well as the still unfolding SolarWinds hack, Neil Daswani will also lay the groundwork for a roadmap to recovery based on the root causes. About Neil Daswani: Neil Daswani is a Co-Director of the Stanford Advanced Security Certification Program. In the past, he has served in a variety of research, development, teaching, and executive roles at Symantec, LifeLock, Twitter, Dasient, Google, NTT DoCoMo USA Labs, Yodlee, and Bellcore. | Neil Daswani Neil has been both a security entrepreneur having co-founded Dasient, which was acquired by Twitter, and has also served as a Chief Information Security Officer at LifeLock and at Symantec’s Consumer Business Unit. His DNA is deeply rooted in security research and development: he has dozens of technical articles published in top academic and industry conferences (ACM, IEEE, USENIX, RSA, BlackHat, and OWASP), and he has been granted over a dozen U.S. patents. Neil is also co-author of “Foundations of Security: What Every Programmer Needs To Know” (http://tinyurl.com/33xs6g). He earned Ph.D. and M.S. degrees in Computer Science at Stanford University, and he holds a B.S. in Computer Science with honors with distinction from Columbia University. |
| Big Breaches Get your copy now so you can have it signed by the author. https://www.amazon.com/Big-Breaches-Cybersecurity-Lessons-Everyone/dp/1484266544 ABOUT THE BOOK The Capital One breach, the Facebook and Cambridge Analytica Hacks, the Marriott Breach, the Office of Personnel Management breaches, the Yahoo breaches, the Equifax breach, and other breaches we cover in this book are some of the worst, most infamous breaches to date. This book covers the root causes of each of these breaches in addition to over 9,000 other reported breaches to date as well as the impact to the financial, social, and political impact of them. | https://bigbreaches.com/ Learn why people should enter the cybersecurity field and what they can do to help prevent breaches from happening in the future. George Santayana once said, “Those who cannot remember the past are condemned to repeat it.” For those both entering and currently, in the field, the first step is to know the biggest breaches of the past, and the next step is to always remember them like the back of their hands to avoid having them repeated. Those who cannot remember the past are condemned to repeat it. -George Santayana |
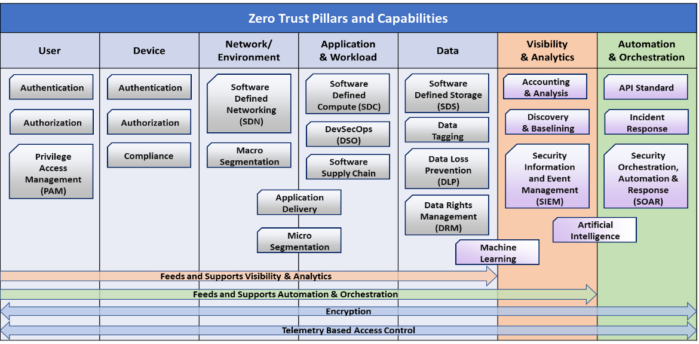
| 5 PM Topic: Z Action Plan and the Regulatory Road Ahead This closing conversation is an overview of the CSA Zero Trust Working Group and key resources to accomplishing your Z-Action Plan. The revamped CSA ZT Research working group aims to help develop and socialize Zero Trust standards and guidance for secure cloud, hybrid, and mobile endpoint environments. This group will have nine distinct workstreams that address specific aspects of an end-to-end ZT architecture and implementation. Zero Trust as a Philosophy & Guiding Principle Zero Trust Organizational Strategy & Governance Pillar: Identity Pillar: Device Pillar: Network/Environment Pillar: Applications & Workload Pillar: Data Automation, Orchestration, Visibility & Analytics Zero Trust Architecture, Implementation, and Maturity Model New ZT working group members can sign up at https://csaurl.org/zt-signup. Link to workgroup charter: Zero Trust Working Group Charter 2022 – Final V1 Each workstream is developing its own mini-charter in its own shared document folder. Additional CSA ZT Resources: CSA ZT Resource Hub: https://cloudsecurityalliance.org/zt/resources/ CSA ZT Slack: csa-public.slack.com – #zero-trust-working-group. Join using this URL: https://csaurl.org/csa-public-slack | Robin Basham Owner EnterpriseGRC Solutions, President, ISC2 East Bay, Certified Information Systems Security (CISSP), Audit (CISA), Governance (CGEIT) and Risk (CRISC-NA), ICT GRC expert and early adopter in both certifying and offering certification programs for Cloud Security and Virtualization, Robin’s industry experience includes the management of systems, controls, and data for SaaS (IaaS and PaaS), Finance, Healthcare, Banking, Education, Defense, and High Tech. Positions held include Technology Officer at State Street Bank, Leading Process Engineering for a major New England CLEC, Sr. Director Enterprise Technology for multiple advisory firms, founding, engineering product, and running two governance software companies, and most recently Director Enterprise Compliance for a major player in the mortgage industry, Ellie Mae. Recently full-time at Cisco, Unified Compliance and ISMS Program Manager, Robin provides voluntary support to social platform security to further social democracy. |
| About EnterpriseGRC Solutions: EnterpriseGRC Solutions is a Governance Risk and Compliance company specializing in mapping cloud security and cyber security frameworks. We implement governance, ISMS, Risk Frameworks, and compliance automation products and programs. We emphasize system-based policies specific to security settings for secure configuration management. | EnterpriseGRC is a women-owned small business offering compliance readiness, Security & GRC tools, Enterprise Security Architecture, Cybersecurity Risk Assessment, and a wide variety of resources for security and GRC technology support. |
| Chapter Announcements Erica Cunningham, Maura Jones, Cory Brown, Peter Chen, | ISC2 East Bay is extremely grateful to Oracle for providing us with the use of their facilities. |
| Big Breaches Book Raffle | Book Signing – Inviting all authors. |
We look forward to seeing you on Friday, March 10th, 2023
Sign in and sponsor breakfast starting at 8 AM, with presentations from 9 AM – 5 PM
Full attendance for registered ISC2 members is 8 CPE. Certificates of attendance may be used with organizations recognizing ISC2 as a resource for professional development. Your end of day feedback will secure your personal recognition of attendance.
Venue: Oracle, Pleasanton – address and map 5815 Owens Dr, Pleasanton, CA 94588
A Note About DoGood
Our board is constantly solicited for opinions and opportunities. You might ask, who has the time? The answer would be, our President and Recent Past Treasurer, Gary Dylina. Through the company, DoGood, we have been able to raise charitable contributions from numerous CyberSecurity oriented companies. We invite all of our members to explore DoGood and make the time to engage Vendors in social good. The reason ISC2 East Bay has operated for so long without asking our members for dues is because our board and our presenters simply do good.




