July 12th, 2019 9:00 AM – 5:30 PM Sitemap
|
Venue: SABA Software4120 Dublin Blvd. Amenity Hub, Dublin, CA 94568 |
|
| This one-day security track includes presentations and labs, light breakfast, lunch, and end of day networking. (ISC)2 East Bay Chapter events facilitate lively discussion and opportunities to extend the presenter wisdom to our real needs in keeping Bay Area companies both competitive and safe. Please learn more at https://isc2-eastbay-chapter.org, LinkedIn, Facebook | ||
| Attendees earn 8 hours of Continuing Professional Education upon Lab completion, survey monkey and sign off. Security at the Speed of DevOps <ISC2 East Bay Summer 2019 Training Flyer> Learn more at https://isc2-eastbay-chapter.org, LinkedIn, Facebook | ||
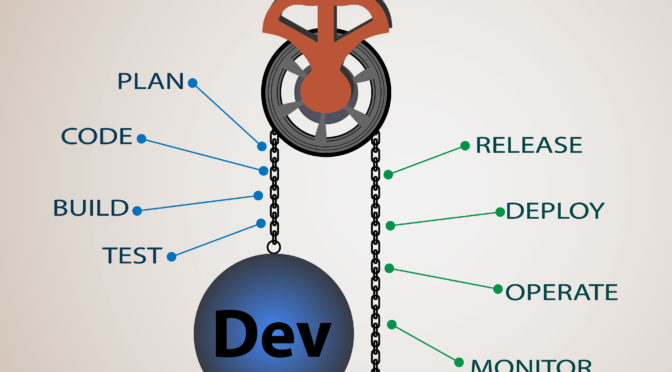
| Theme – Security at the speed of DevOps
Security at the speed of DevOps theme includes 5 speaker instructors and guided product demonstrations offering 8 CPE for full attendance. Learn more at https://isc2-eastbay-chapter.org, LinkedIn, Facebook. Three opportunities for networking with your peers
As a result of our generous sponsors, ALL of the money collected at this event will go to scholarship. If you are experiencing hardship and wish to attend, please have proof of (ISC)2 membership or ISACA membership and reach out to Director Education & Career Development Jing Zhang-Lee, or Conference Director Robin Basham *If you are not a member of ISC2 or ISC2 East Bay Chapter, please complete the membership application form and send the application with your notice of intent to attend. Membership is still free, but we do need to know who you are. Something new: Technology Book Exchange Table Our Board has a collection of great technology books that we are going to put out for free at the event. You are welcome to take any and as many as you want. Any books that you bring and don’t get selected need to go home with you, … so sell those ideas to a new reader. |
|
|
For all Registered Guests – Please give yourself a half-hour to enjoy Bagels and Coffee Breakfast Sponsored by 
|
||
| Session 1: 9:00-10:00 AM | Meet Ellen Boehm | |
The Importance of Managing Code Signing CertificatesEllen Boehm, Director of Product Management – Keyfactor Control |
As Director of Product Management, Ellen leads the product strategy and go to market approach for the Keyfactor Control platform, focusing around solutions for the IoT market. Ellen has 15+ year’s experience leading new product development with a focus on IoT and connected products in Lighting controls, Smart Cities, Connected buildings and Smart Home technology. |
|
| Session 1: How to Protect Code Signing Certificates – The Keyfactor Secure Code Signing Module locates and transfers all code signing certificates from Enterprise network locations (including all networked PC, storage, and thumb drives) to a secure vault. Once inside the certificates never leave the vault. A user with appropriate access presents the code to be signed to the module where it’s signed and returned to the user. Access controls are in place to ensure that only those with the right privileges can sign software and firmware. Join us and learn how to improve the security of your Code Signing procedures.
About: Keyfactor, formerly Certified Security Solutions (CSS), is a leading provider of secure digital identity management solutions that enables organizations to confirm authenticity, and ensure the right things are interacting in the right ways in our connected world. From an enterprise managing millions of devices and applications that affect people’s lives every day, to a manufacturer aiming to ensure its product will function safely throughout its life cycle, Keyfactor empowers global enterprises with the freedom to master every digital identity. Its clients are the most innovative brands in the industries where trust and reliability matter most. Website https://www.keyfactor.com |
||
| Ohhhh Nooooo | We’ll Meet Dorian Cougias: next time!!! | |
|
|
 |
 |
Remember to thank  for the steady supply of coffee, sodas, water and juice for the steady supply of coffee, sodas, water and juice |
||
| Session 2 10:00 to 10:45 | We are organizing a panel | |
| So you’ve committed to working your program to an Agile Methodology: Now What? |  |
Before After After |
| Announcements – quick bio break – get a coffee refresh, sit back down! | ||
| Session 3: 11:00- 11:55 | Meet Dave Karow | |
| Safe At Any Speed
Split Software Dave Karow is the Continuous Delivery Evangelist at Split Software. |
Dave regularly gives talks at vendor-neutral technical conferences, and will be speaking at Agile/DevOps East in Orlando on “Feature Flagging: Proven Patterns for Control & Observability in Continuous Delivery.” Before Split, Dave helped development teams democratize “shift left” performance testing for BlazeMeter.com.
|
 |
| Session 3: The goal of DevOps is to deliver value faster. Modern teams ship smaller releases, observe the impact on system and user behavior and iterate based on those observations in a fast and virtuous loop. The good news for security professionals is that this style of digital transformation isn’t just about pushing out features and functions faster (a scary thought), but about having more fine-grained control of exposure and building-in observability so they gain both safety and speed. One large financial firm found that adopting modern DevOps made them safer AND faster than their legacy compliance regimen. If your goal is to shift-left security awareness in your organization and to partner with developer teams to build in security as they build minimum viable products and iterate on them, this talk will catch you up on critical capabilities that make this new way of work possible. After the talk and Q&A, Dave will give away several copies of Accelerate, Building and Scaling High Performing Technology Operations by Nicole Forsgren, Jez Humble and Gene Kim.
|
||
| LUNCH – Sponsored by SEPIO | Panera Brown Bag | |
| Lunch Lead by Sepio | ||
| Session 4: 1:00 to 2:00 | Meet Yossi Appleboum | |
Rogue Device Mitigation: Revolutionary Protection Against the Rapidly Changing Landscape for Cyber-Attacks
|
The Latin word “Sepio” means “defend” and “guard.” Sepio is disrupting the cyber-security industry by uncovering hidden hardware attacks. Bad actors are gaining access by implanting rogue hardware – Sepio’s Rogue Device Mitigation (RDM) stops them. The company was founded by cyber security experts from private industry and government agencies. |  Our team has earned global recognition and decoration in fighting attacks though malicious hardware devices. Website http://www.sepio.systems Our team has earned global recognition and decoration in fighting attacks though malicious hardware devices. Website http://www.sepio.systems
Yossi Appleboum, CEO, Sepio Systems |
 |
||
| Session 5: 2:00-2:30 | REALLY Meet Angel Mazzucco | People are Sweet! |
Is it People, Process or Technology?“Yes, but it’s the people who make it sweet” Visionary. Problem solver. Ambitious. Giver. Rapid Learner. Always Hungry. Entrepreneur. Genuine Leader. |
YOU CAN CALL ME ANGEL: I have an unquenchable thirst for knowledge and an immense interest in people; knowing what they like to do, how they respond to situations, and the overall human operating model. I love different perspectives, and ideas. I’ve learned even when you deserve something, that doesn’t mean it’s going to be handed to you. You need to strive for the things you want. |
I am a hard worker. I set goals, and accomplish them. I push myself, and compel others to achieve their own definition of success through strategy, encouragement, and action. |
| Being a leader, I go through life with patience, respect for others, and determination, all while making sure to have the most fun I can while doing so! I am always moving forward. I don’t give up, even when everyone else does. I’ve learned it’s not about your resources, but rather how resourceful you are. I love a good challenge, and feel most aligned when solving problems. I am strong and reliable. I set the bar high, because I know anything is possible.
My current obsessions are within data and cyber security. My curiosities are around emerging technologies like A.I. and Machine Learning. (Let’s understand why intentions like this matter.) |
||
| Networking 2:30-2:45 PM |
Sponsored by KFORCE |
We Break 4 Cake |
|
Special thanks to Maura Jones and Asha Kumar for coordinating meals. |
 |
 Call out to Angel Mazzucco who organizes real interviews for real jobs, and brings us CAKE!! Call out to Angel Mazzucco who organizes real interviews for real jobs, and brings us CAKE!! |
| Session 6 2:45-3:30 | Meet Steven Gautier | Meet Ferry de Koning |
| Deployed in minutes: Cloud Based HSM on Demand for DEVOPS
|
Gemalto is an international digital security company providing software applications, secure personal devices such as smart cards and tokens, and managed services. It is the world’s largest manufacturer of SIM cards. The company was founded in June 2006 when two companies, Axalto and Gemplus International, merged. | 
|
|
Ferry de Koning has a Bachelor in Computer Science/Electronics and Studied Business Information Technology at the University of Twente, The Netherlands. 20+ years experience in Strategic ICT Consultancy, Digital Banking and Payment, Building IT operations, Business Development and Sales. Worked for KLM, KPMG, CGI, GEMALTO, THALES, TRIVNET and the Dutch Army in a variety of roles. In the last couple of years as part of his Business Development Role promoting cyber security solutions, especially Data Protection on Demand and creating mutual beneficiary Technology/VAR partnerships. He holds a dual citizenship of Israel and The Netherlands. He currently lives in Austin, Texas. His live motto is Luctor and Emergo (I struggle and emerge).
|
||
| Session 8 3:30-4:15 | Meet Eric Butler | |
Securonix |
The Sales Engineering space has been my calling since an instructor turned me onto the field in Network 101. The blend of business & tech has given growth opportunities that purist jobs can’t. My record illustrates a consistent & gapless track record pursuing & achieving this goal. This success is also seen in several of the companies with I’ve had the privilege to work, leading to acquisition or IPO. My path to this point has been tailored to gain the broadest exposure to diverse security controls to drive customer & company success. | Skilled in Azure & AWS security, Windows & Linux Server cybersecurity, and organizational risk assessment. Strong sales professional with a Network and Communications Management focus in Security Systems Networking and Telecommunications.” Learn more http://www.securonix.com |
 |
||
| Session 9 4:15-5:00 | Member Meeting | Snacks, networking, surveymonkey |
| Voting Members will gather to complete a spot election for the newly vacant role of Chapter President and to nominate new faces to the roles of Director Operations and Membership Director- All others are welcome to sign up for private time with your favorite product SME, Security Mentor or Hiring Manager. This time counts for 1 CPE. | Sepio, Split, Cisco, Gemalto, KeyFactor, UCF, DevOps Mentors (board and speakers), Follow up time for the live labs. What worked, what challenged us? Attendees will not receive CPE unless they return their survey monkey and write up their final activity |  |
We will not be coordinating dinner, however Gemalto and KeyFactor have extended an invitation for board, committee, sponsors and speakers to meet for drinks. We made a decision to lower costs for attendees by skipping the price of dinner. People who want to meet later for drinks should let the us know. |
||
 |
||
| Saba Software, meeting sponsor, thanks for supplying our venue and many contributing members of the conference committee | The average person will spend nearly 100,000 hours of their life working. Saba’s mission is to help our clients create a work experience for their people that’s more engaging, inspiring and empowering — an experience that can transform the working lives of millions, and creates more growth and success for every business.
With Saba, you have the power of 1,400 talent experts in your corner, solely focused on living that mission, and helping HR leaders transform their people strategy and talent experience, while delivering tangible impact to the business. |
|
| KeyFactor, meeting sponsor, thanks for supplying speaker and dinner | Keyfactor, formerly Certified Security Solutions (CSS), is a leading provider of secure digital identity management solutions that enables organizations to confirm authenticity, and ensure the right things are interacting in the right ways in our connected world. From an enterprise managing millions of devices and applications that affect people’s lives every day, to a manufacturer aiming to ensure its product will function safely throughout its life cycle, Keyfactor empowers global enterprises with the freedom to master every digital identity. Its clients are the most innovative brands in the industries where trust and reliability matter most. Website https://www.keyfactor.com | |
| Sepio Systems, Meeting sponsor, thanks for supplying speaker and dinner | The Latin word “Sepio” means “defend” and “guard.” Sepio is disrupting the cyber-security industry by uncovering hidden hardware attacks. Bad actors are gaining access by implanting rogue hardware – Sepio’s Rogue Device Mitigation (RDM) stops them. The company was founded by cyber security experts from private industry and government agencies. Our team has earned global recognition and decoration in fighting attacks though malicious hardware devices. Website http://www.sepio.systems |  |
| Skybox Security, Gold sponsor, live demonstration assigning the policy that proves our governance is in place | Best-in-class Cybersecurity Management Software The software uses analytics to prioritize on organization’s risk exposures and recommends informed action to best address those exposures. These capabilities extend across highly complex networks, including those in physical, virtual, cloud and operational technology (OT) environments. By integrating with more than 120 networking and security technologies, the company’s broad platform, the Skybox™ Security Suite, enables organizations to reduce security risks that attackers can find and exploit, such as device misconfigurations and policy violations, as well as exposed and unpatched vulnerabilities. Established in 2002, Skybox is a privately held company with worldwide sales and support teams serving an international customer base of more than 500 enterprises in over 50 countries. |
 |
| Netskope, Platinum Sponsor, live demonstration, mapping the path of business, the evolution of cloud security | Netskope is the leader in cloud security. Using patented technology, Netskopeís cloud-scale security platform provides context-aware governance of all cloud usage in the enterprise in real time, whether accessed from the corporate network, remote, or from a mobile device. This means that security professionals can understand risky activities, protect sensitive data, stop online threats, and respond to incidents in a way that fits how people work today. With granular security policies, the most advanced cloud DLP, and unmatched breadth of workflows, Netskope is trusted by the largest companies in the world. Netskope ó security evolved. |  |
| Cybereason, Meeting sponsor, thanks for supplying speaker and dinner | Cybereason is the leader in endpoint protection, offering endpoint detection and response, next-generation antivirus, managed monitoring and IR services. Founded by elite intelligence professionals born and bred in offense-first hunting, Cybereason gives enterprises the upper hand over cyber adversaries. The Cybereason platform is powered by a custom-built in-memory graph, the only truly automated hunting engine anywhere. It detects behavioral patterns across every endpoint and surfaces malicious operations in an exceptionally user-friendly interface. Cybereason is privately held and headquartered in Boston with offices in London, Tel Aviv, and Tokyo. |
 |
| Gemalto | Gemalto is an international digital security company providing software applications, secure personal devices such as smart cards and tokens, and managed services. It is the world’s largest manufacturer of SIM cards. The company was founded in June 2006 when two companies, Axalto and Gemplus International, merged. |  |
| CyberArk, Platinum, contributes lab leaders and speakers in addition to actively sponsoring the last four conference events | CyberArk is the only security company laser-focused on striking down targeted cyber threats, those that make their way inside to attack the heart of the enterprise. Dedicated to stopping attacks before they stop business, CyberArk is trusted by the worldís leading companies ó including more than 45% of the Fortune 100 companies ó to protect their highest value information assets, infrastructure, and applications. For over a decade CyberArk has led the market in securing enterprises against cyber attacks that take cover behind insider privileges and attack critical enterprise assets. Today, only CyberArk is delivering a new category of targeted security solutions that help leaders stop reacting to cyber threats and get ahead of them, preventing attack escalation before irreparable business harm is done. At a time when auditors and regulators are recognizing that privileged accounts are the fast track for cyber attacks and demanding stronger protection, CyberArkís security solutions master high-stakes compliance and audit requirements while arming businesses to protect what matters most. With offices and authorized partners worldwide, CyberArk is a vital security partner to more than 3,200 global businesses, including more than 45% of the Fortune, 100 more than 25% of the Global 2000, CyberArk has offices in the U.S., Israel, Australia, France, Germany, Italy, Japan, Netherlands, Singapore, Spain, Turkey and the U.K. |  |
| The Unified Compliance Framework® (UCF) Silver Sponsor, provides speakers and lab based trainings. UCF is an ISC2 partner in providing certifications for controls and compliance mapping. | The Unified Compliance Framework® (UCF) was created by Dorian Cougias and his research partner, Marcelo Halpern of the international law firm Perkins Coie, which oversees all legal aspects of the UCF. This patented GRC framework is used as a core component of advanced GRC solutions by leading software publishers, certified auditors and consultants worldwide. – Unified Compliance’s dynamic SaaS portal, the Common Controls Hub, provides a new interface to the UCF that aids in extracting needed data from the framework easily and helps compliance professionals keep pace with the ever-evolving regulatory demands, confidently manage risk, and ease resource and budget barriers. The Common Controls Hub gives users rapid access to its massive data repository of more than 90,000 individual mandates from 800-plus laws and standards from around the globe. Sorting through the most up-to-date demands, figuring out which controls they need to implement and how they overlap is now a quick process with just a few simple mouse clicks. – The Common Controls Hub simplifies the need to locate, research, interpret, and reconcile new and evolving mandates by giving compliance professionals the ability to centrally scope, define and maintain regulatory demands online. Companies can now automatically compile custom, harmonized control lists in minutes by vertical industries, market segments, and geographies.” |  |
| Securonix, recent past Platinum Sponsor, always a welcome participant at (ISC)2 East Bay Events | Securonix is working to radically transform all areas of data security with actionable security intelligence. Our purpose-built advanced security analytics technology mines, enriches, analyzes, scores and visualizes customer data into actionable intelligence on the highest risk threats from within and outside their Using signature-less anomaly detection techniques that track users, account, and system behavior, Securonix is able to automatically and accurately detect the most advanced cyber threats, insider threats, and fraud attacks. Globally customers are using Securonix to address the most basic and complex needs around insider threat detection and monitoring, high | 
privileged activity monitoring, data exfiltration, enterprise and web fraud detection, application risk monitoring, cloud security monitoring, cyber threat monitoring, and access risk management. Securonix uses a Hadoop platform to provide unlimited scalability and open data model. http://www.securonix.com |
 |
||
| How to become a member: Please directly contact our Chapter President Lee Neely and fill out the membership form https://isc2-eastbay-chapter.org/membership/ | ||
 |
 |
Thank you Chevron, for providing us space and food for the last two years. |
| Blackhawk | Oracle |
|
| (This 1-day event counts towards 6 hours of Continuing Professional Education CPE) | ||
Your friends and colleagues at (ISC)2 East Bay Chapter chapter can’t wait to see you. We hope you join us in giving special thanks to the conference committee volunteers, without whom, such events would not be possible. Providing weekly meetings, binding flyers, drafting letters, being a liaison to our gracious speakers, updating and proofing our brochures, and assisting in the overall quality management of the Summer Conference, we acknowledge Ash Kumar, Dan Green, Atul Kumar, Maura Jones, Ana Colocho, Rizwan , Austin and others as well as all members of the Board of Directors for their added responsibilities in coordinating our conference business, and for all the wisdom provided by the full membership. Your support is greatly appreciated.Yours Sincerely,
The (ISC)2 East Bay Chapter Board of Directors
Recent Past Presidents are Lokesh Sisodiya, Tom Rogers and Lee Neely |
||

 Thank you Rizwan and All of Saba Software for your hosting of our tremendous event.
Thank you Rizwan and All of Saba Software for your hosting of our tremendous event.










